Hey there!
We are happy to announce that we are officially starting the transition to Bookworm ![]() !
!
If you are familiar with server administration, you may understand that this is a delicate operation even though the Yunohost team will do its best to provide the smoothest possible transition with a one-click upgrade through the webadmin, just like we did in the past for Jessie → Stretch → Buster → Bullseye.

 THIS IS ALPHA-STAGE DEVELOPMENT, WE ABSOLUTELY DISCOURAGE ANY USE OF YUNOHOST 12.x (or running the migration to be shipped in 11.x) ON A PRODUCTION SERVER - IT WILL BREAK !
THIS IS ALPHA-STAGE DEVELOPMENT, WE ABSOLUTELY DISCOURAGE ANY USE OF YUNOHOST 12.x (or running the migration to be shipped in 11.x) ON A PRODUCTION SERVER - IT WILL BREAK ! 

 What to test ?
What to test ?
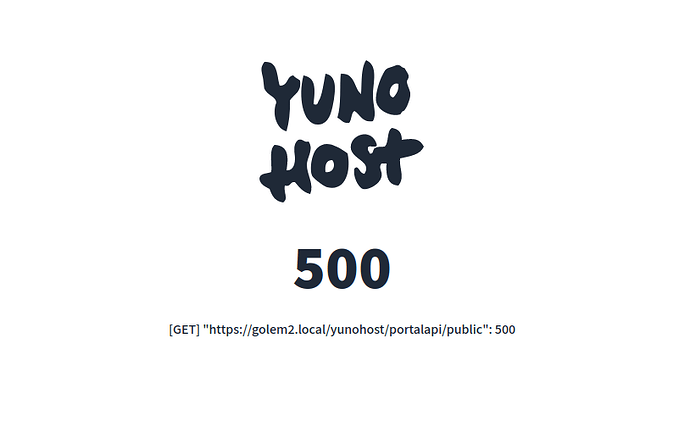
Mainly, YunoHost 12 will come with an important rework of the SSO layer and user portal. We are looking at both general feedback on the UI/UX, and usability in terms of “does it works and behave as expected”.
Installing a fresh YunoHost on top of a fresh Debian 12/Bookworm
- Obtain a brand new server (such as a VPS online, a local virtual machine, or a development LXC)
- Preinstall your server with Debian Bookworm
- Then install Yunohost 12.x with :
$ curl https://install.yunohost.org/bookworm | bash -s -- -d unstable
# You will get a disclaimer intended to make sure what you're doing.
# Read it and follow the instructions.
Apart from validating that the install does work, we encourage you to test every apps and features that you would typically use in a real-life server (so including the webadmin, the user portal, diagnosis, certificates, emails, …). Note that some apps are still known to not support Bookworm yet and require fixes from our side.
Migrating an existing YunoHost 11/Bullseye server
![]() This is still work in progress
This is still work in progress ![]() , cf https://github.com/YunoHost/yunohost/pull/1759
, cf https://github.com/YunoHost/yunohost/pull/1759
 Preliminary changelog
Preliminary changelog
 Major changes
Major changes
- The install script has been reworked with a simpler flow and UI (instead of the old ncurses/whiptail)
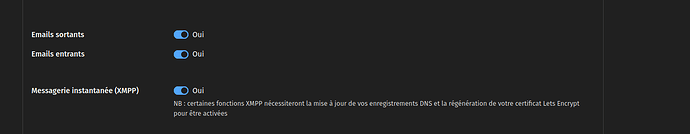
- Do not install mariadb, php-fpm, metronome and rspamd by default
- FIXME: rspamd is actually used not just for spam filtering but also DKIM signing and verifying, will need to look at opendkim as replacement
- Completely rework SSOwat and the user portal, split into three distinct pieces:
- SSOwat only handling only the SSO/ACL logic (nginx lua middleware)
- A new “portal API” (yunohost-portal-api) service delivering authentication cookies and allowing users to retrieve/update infos
- A new portal front end (yunohost-portal)
 Regarding the new portal
Regarding the new portal
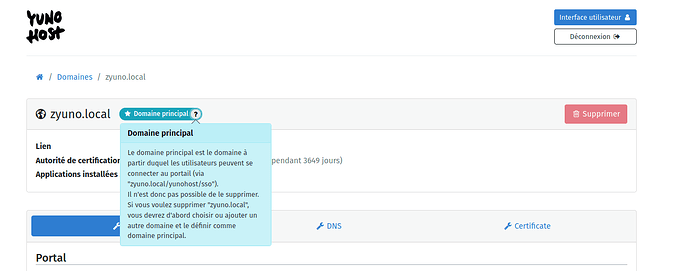
- The portal and authentication mechanism are now separated in terms of “main domain trees”. For example,
foo.tldandsub.foo.tldshare the same portal, butbar.tldandapp.bar.tldshare a second, different portal - Users can only access a portal if they have access to at least one app of that “main domain tree”, or if they are admin
- FIXME: we should probably also allow people if their main email is part of that domain tree?
- The new portal include app logos, descriptions, and an optional ‘search engine’ bar.
- FIXME: sooner or later, people will want to be able to change logos and descriptions
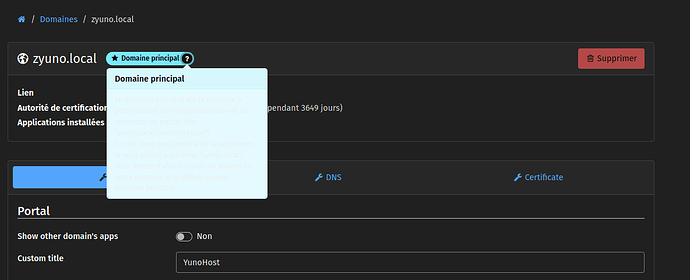
- The new portal’s appearance can be customized from the webadmin in the corresponding “main domain”'s setting (such as changing the portal name, logo, default theme, custom message, …). Each user can also pick the theme in their own settings page.
- Note that if you themed the old portal, this theming won’t be magically migrated to the new portal
- New option to have the list of public apps as “default app”
- The old “yunohost tile overlay” doesn’t exist anymore
- It is technically possible to write a completely different and independent user portal (as long as it properly interacts with the portal API) FIXME: generate proper documentation for the new portal API, maybe using swagger
Misc/technical
- webadmin: rework cookie/session expiration mechanism. Cookies are now still valid after restarting the API (preventing clumsy disconnect during self-upgrades) and the cookie validity is automatically extended every time an API request is performed.
- various compatibility tweakings for Bookworm
- regenconf: update nginx and dovecot ciphers according to Mozilla recommendation
- regenconf: update fail2ban config
- configpanels: refactor to use pydantic for more typing and consistency, add proper autogenerated doc
- apps: Yarn third-party repo is now available by default in apt config just like Sury, no need for an extra apt resource thingy
- apps: drop support for unused
--dedicated_servicein php helpers - apps: drop support for legacy LUA-style regexes in permission urls
- apps: do not auto-patch old PHP versions anymore because Sury is enabled by default and allows the install of arbitrary PHP versions
- apps: drop support of the legacy
unprotected_uris,redirected_urland similar settings - cli: drop support for legacy
firstname/lastnameargs inyunohost user create - cli: drop legacy
yunohost domain dns-confandyunohost domain cert-status,cert-install,cert-renew - perf: minimize regen-conf calls to
yunohost settings get, and other misc lazy-loading optimizations - quality: simplify the logging mess
- quality: rework ci tests workflow