For the past months, I’ve been exposing my home server running yunohost to the internet using zerotier tunnels connected to nginx reverse proxies on a VPS. (my exact configuration is described here)
This has been working well for me for most apps, without having to do any port forwarding or dynamic dns.
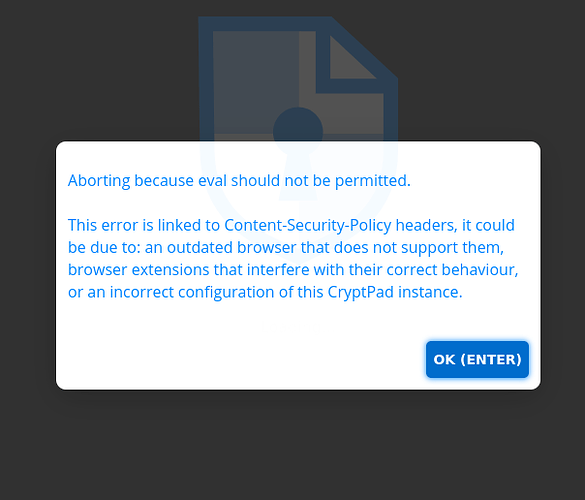
However Cryptpad is not working for me and displays a warning when I open a document. In chrome in the iframe it says its unable to connect to sandbox-crypt.commoninternet.net. In firefox I see this warning:
I’ve created https certificates and reverse proxies to the tunnel for both crypt.commoninternet.net and sandbox-crypt.commoninternet.net, and they both independently load and show a valid certificate… but I guess still won’t play nicely together via iframes?
I also had an issue with OnlyOffice in NextCloud which seemed like some type of iframe issue – this was fixable by installing Ignore-X-Frame firefox extension, but I still haven’t figured out how to make it work without the extension.
I did a fresh install of Cryptpad directly on the VPS, without any of the tunelling, and it worked fine like that, which is making me think I am not understanding something about the reverse proxy and tunneling, that is actually causing problems with iframes (and maybe something about CSP or x-frame options), even though I had the impression that since there is an HTTPs certificate on the VPS, it would be identical. But maybe its something about the details of HTTPs I don’t understand?
If anyone has any ideas what it could be or how to fix it, any ideas appreciated.
I love having the home server accessible to the internet without having to do port forwarding or reveal its home IP address, so I would hate to have to ditch this setup because of this iframe issue.