Salut,
J’ai installé Custom Webapp. Mais lorsque je tente d’accéder au FTP avec FileZilla, j’obtiens un : connexion reset by peer…
Quelqu’un peut-il m’aider ?
Salut,
J’ai installé Custom Webapp. Mais lorsque je tente d’accéder au FTP avec FileZilla, j’obtiens un : connexion reset by peer…
Quelqu’un peut-il m’aider ?
Alors, s’il s’agit de la version a jour, il s’agit d’un accès sftp (port 22) et pas FTP. Les infos sont dispo sur l’index affiché a la racine de ta webapp.
FileZilla est tout indiqué pour ça.
Justement, j’ai entré le bon nom d’utilisateur, il s’agit de la nouvelle App. Je me connecte bien en SFTP, et j’ai toujours cette erreur.
Voilà l’erreur
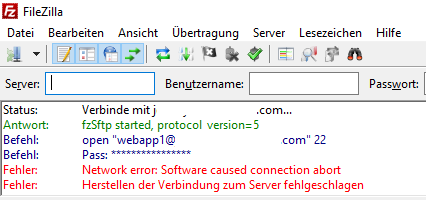
Personne ne peut m’aider ?
J’ai tenté une réinstallation de l’application, et j’ai toujours le même problème ! Cela devient gênant car je ne peux plus publier mes articles…
Pour rappel; voici l’erreur : Fehler: Connection reset by peer
C’est ton serveur qui rejette la connexion.
Si tu as suivi la doc pour sécuriser ta connexion SSH, en particulier limiter les users autorisés à se connecter, l’user créer pour le sftp de ta webapp n’est pas autorisé.
Le script ajoute simplement un chroot sftp:
Il faut vérifier le contenu du fichier de config du serveur ssh, /etc/ssh/sshd_config
Que dois-je faire dans ce fichier ?
A savoir que je n’ai jamais modifié le fichier, sauf pour autoriser le root à se loguer.
Donc tu l’as modifié.
Vérifie la config, en particulier les directives Port, AllowUsers et PasswordAuthentication
Je ne vois rien d’anormal… Comment je fais pour copier coller tout le contenu du fichier pour l’envoyer ici ? Je ne me souviens plus de la commande pour le mettre sur yunohost.
Tu devrais retrouver ça sur le forum, je ne connais pas la commande de mémoire.
Sinon, tu peux simplement poster le contenu concerné ici.
> # Package generated configuration file
> # See the sshd_config(5) manpage for details
> # What ports, IPs and protocols we listen for
> Port 22
> # Use these options to restrict which interfaces/protocols sshd will bind to
> ListenAddress ::
> ListenAddress 0.0.0.0
> Protocol 2
> # HostKeys for protocol version 2
> HostKey /etc/ssh/ssh_host_rsa_key
> HostKey /etc/ssh/ssh_host_dsa_key
> #Privilege Separation is turned on for security
> UsePrivilegeSeparation yes
> # Lifetime and size of ephemeral version 1 server key
> KeyRegenerationInterval 3600
> ServerKeyBits 768
> # Logging
> SyslogFacility AUTH
> LogLevel INFO
> # Authentication:
> LoginGraceTime 120
> PermitRootLogin no
> StrictModes yes
> RSAAuthentication yes
> PubkeyAuthentication yes
> #AuthorizedKeysFile %h/.ssh/authorized_keys
> # Don't read the user's ~/.rhosts and ~/.shosts files
> IgnoreRhosts yes
> # For this to work you will also need host keys in /etc/ssh_known_hosts
> RhostsRSAAuthentication no
> # similar for protocol version 2
> HostbasedAuthentication no
> # Uncomment if you don't trust ~/.ssh/known_hosts for RhostsRSAAuthentication
> #IgnoreUserKnownHosts yes
> # To enable empty passwords, change to yes (NOT RECOMMENDED)
> PermitEmptyPasswords no
> # Change to yes to enable challenge-response passwords (beware issues with
> # some PAM modules and threads)
> ChallengeResponseAuthentication no
> # Change to no to disable tunnelled clear text passwords
> #PasswordAuthentication yes
> # Kerberos options
> #KerberosAuthentication no
> #KerberosGetAFSToken no
> #KerberosOrLocalPasswd yes
> #KerberosTicketCleanup yes
> # GSSAPI options
> #GSSAPIAuthentication no
> #GSSAPICleanupCredentials yes
> X11Forwarding yes
> X11DisplayOffset 10
> PrintMotd no
> PrintLastLog yes
> TCPKeepAlive yes
> #UseLogin no
> #MaxStartups 10:30:60
> Banner /etc/issue.net
> # Allow client to pass locale environment variables
> AcceptEnv LANG LC_*
> Subsystem sftp internal-sftp
> # Set this to 'yes' to enable PAM authentication, account processing,
> # and session processing. If this is enabled, PAM authentication will
> # be allowed through the ChallengeResponseAuthentication and
> # PasswordAuthentication. Depending on your PAM configuration,
> # PAM authentication via ChallengeResponseAuthentication may bypass
> # the setting of "PermitRootLogin without-password".
> # If you just want the PAM account and session checks to run without
> # PAM authentication, then enable this but set PasswordAuthentication
> # and ChallengeResponseAuthentication to 'no'.
> UsePAM yes
> Match User sftpusers
> ForceCommand internal-sftp
> ChrootDirectory /home/%u
> AllowTcpForwarding no
> GatewayPorts no
> X11DisplayOffset 10
> PrintMotd no
> PrintLastLog yes
> TCPKeepAlive yes
> #UseLogin no
> #MaxStartups 10:30:60
> Banner /etc/issue.net
> # Allow client to pass locale environment variables
> AcceptEnv LANG LC_*
> Subsystem sftp internal-sftp
> # Set this to 'yes' to enable PAM authentication, account processing,
> # and session processing. If this is enabled, PAM authentication will
> # be allowed through the ChallengeResponseAuthentication and
> # PasswordAuthentication. Depending on your PAM configuration,
> # PAM authentication via ChallengeResponseAuthentication may bypass
> # the setting of "PermitRootLogin without-password".
> # If you just want the PAM account and session checks to run without
> # PAM authentication, then enable this but set PasswordAuthentication
> # and ChallengeResponseAuthentication to 'no'.
> UsePAM yes
> Match User sftpusers
> ForceCommand internal-sftp
> ChrootDirectory /home/%u
> AllowTcpForwarding no
> GatewayPorts no
> X11Forwarding no
> ##-> my_webapp
> # Hardening user connection
> Match User webapp1
> ChrootDirectory %h
> ForceCommand internal-sftp
> AllowTcpForwarding no
> PermitTunnel no
> X11Forwarding no
> ##<- my_webapp
Edit: utilise le formatage de code au lieu des citations pour poster du code.
Rien d’anormal dans ton fichier de config, tu peux par contre supprimer la section Match User sftpusers en double.
Tu devrais tenter un sftp en ligne de commande avec verbose (sauf si filezilla le permet) pour avoir plus d’infos sur ton erreur.
Trace: Sent password
Trace: Access granted
Trace: Opening session as main channel
Trace: Network error: Software caused connection abort
Fehler: Network error: Software caused connection abort
Trace: CControlSocket::DoClose(64)
Trace: CSftpControlSocket::ResetOperation(66)
Trace: CControlSocket::ResetOperation(66)
Fehler: Herstellen der Verbindung zum Server fehlgeschlagen
Trace: CFileZillaEnginePrivate::ResetOperation(66)
En français ou en anglais, mais pas en allemand…
C’est pas un sftp en verbose ça, teste en ligne de commande pour tenter d’avoir plus d’info.
Merci  Peux-tu m’expliquer comment faire un sftp en verbose sous Ubuntu ?
Peux-tu m’expliquer comment faire un sftp en verbose sous Ubuntu ?
http://www.unix.com/man-page/Linux/1/sftp/
sftp -v webapp1@domain.tld
OpenSSH_7.2p2 Ubuntu-4ubuntu1, OpenSSL 1.0.2g-fips 1 Mar 2016
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: /etc/ssh/ssh_config line 19: Applying options for *
debug1: Connecting to blabla.com [2a01:…] port 22.
debug1: Connection established.
debug1: permanently_set_uid: 0/0
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_rsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_rsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_dsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_dsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_ecdsa type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_ecdsa-cert type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_ed25519 type -1
debug1: key_load_public: No such file or directory
debug1: identity file /root/.ssh/id_ed25519-cert type -1
debug1: Enabling compatibility mode for protocol 2.0
debug1: Local version string SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu1
debug1: Remote protocol version 2.0, remote software version OpenSSH_6.7p1 Debian-5+deb8u2
debug1: match: OpenSSH_6.7p1 Debian-5+deb8u2 pat OpenSSH* compat 0x04000000
debug1: Authenticating to blabla.com:22 as 'webapp1’
debug1: SSH2_MSG_KEXINIT sent
debug1: SSH2_MSG_KEXINIT received
debug1: kex: algorithm: curve25519-sha256@libssh.org
debug1: kex: host key algorithm: ssh-rsa
debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: compression: none
debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: compression: none
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
debug1: Server host key: ssh-rsa SHA256:2r0C4Zg…
debug1: Host ‘blabla.com’ is known and matches the RSA host key.
debug1: Found key in /root/.ssh/known_hosts:3
debug1: rekey after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug1: rekey after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS received
debug1: SSH2_MSG_SERVICE_ACCEPT received
Debian GNU/Linux 8
debug1: Authentications that can continue: publickey,password
debug1: Next authentication method: publickey
debug1: Trying private key: /root/.ssh/id_rsa
debug1: Trying private key: /root/.ssh/id_dsa
debug1: Trying private key: /root/.ssh/id_ecdsa
debug1: Trying private key: /root/.ssh/id_ed25519
debug1: Next authentication method: password
webapp1@blabla’s password:
debug1: Authentication succeeded (password).
Authenticated to blabla.com ([2a01:]:22).
debug1: channel 0: new [client-session]
debug1: Requesting no-more-sessions@openssh.com
debug1: Entering interactive session.
debug1: pledge: network
packet_write_wait: Connection to 2a01:*** port 22: Broken pipe
Couldn’t read packet: Connection reset by peer
Et tes connexions ssh ne posent aucun problème ?
Jette un coup d’oeil à syslog, le serveur répond correctement mais coupe la connexion. Sshd doit loguer quelque chose.