Hey,
I think we are getting there. Thanks @rungeard and @charly for all you help on this!!
Im running a VPS on Hetzner.com, Yunohost server as a local VM and wireguard for connection.
Before going in to details I think there is a problem with coturn start-up sequence vs network connections (and/or wg?) that has to be solved, many reboots on YH-server fails to start/or even get this in correct order!!
I have not tested this yet, but found this - coturn/coturn.service at master · coturn/coturn · GitHub
Edit: I think we found a workaround for this problem, its described here: Tutorial : How to make matrix-synapse's coturn (audio & video calls) work behind a VPN - #9 by tomas
I followed @rungeard tutorial here - Homemade WireGuard VPN on a VPS server
My wg NAT settings are:
VPS settings
# PostUp.sh VPS
iptables -A FORWARD -i wg0 -j ACCEPT;
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE;
ip6tables -A FORWARD -i wg0 -j ACCEPT;
ip6tables -t nat -A POSTROUTING -o eth0 -j MASQUERADE;
# icmp
iptables -A INPUT -p icmp -j ACCEPT;
ip6tables -A INPUT -p ipv6-icmp -j ACCEPT;
# Routing TCP port 25 and 587 from Yunohost Server to internet
for j in 25 587
do
iptables -t nat -A POSTROUTING -s 10.6.0.2 -p tcp --dport $j -j SNAT --to 98.76.543.210;
iptables -A FORWARD -s 10.6.0.2 -p tcp --dport $j -j ACCEPT;
ip6tables -t nat -A POSTROUTING -s fd42:42:42::2 -p tcp --dport $j -j SNAT --to aaaa:bbbb:cccc:dddd::1;
ip6tables -A FORWARD -s fd42:42:42::2 -p tcp --dport $j -j ACCEPT;
done
# Routing TCP port required from VPN server to Yunohost server
for i in 25 80 140 443 587 993 5222 5269 8448
do
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport $i -j DNAT --to-destination 10.6.0.2;
iptables -A FORWARD -d 10.6.0.2 -p tcp --dport $i -j ACCEPT;
ip6tables -t nat -A PREROUTING -i eth0 -p tcp --dport $i -j DNAT --to-destination fd42:42:42::2;
ip6tables -A FORWARD -d fd42:42:42::2 -p tcp --dport $i -j ACCEPT;
done
# synapse contur
for port in udp tcp
do
for i in 5350 5349
do
iptables -t nat -A PREROUTING -i eth0 -p $port --dport $i -j DNAT --to-destination 10.6.0.2;
iptables -t nat -A POSTROUTING -s 10.6.0.2 -p $port --dport $i -j SNAT --to 98.76.543.210;
iptables -A FORWARD -s 10.6.0.2 -p $port --dport $i -j ACCEPT;
iptables -A FORWARD -d 10.6.0.2 -p $port --dport $i -j ACCEPT;
ip6tables -t nat -A PREROUTING -i eth0 -p $port --dport $i -j DNAT --to-destination fd42:42:42::2;
ip6tables -t nat -A POSTROUTING -s fd42:42:42::2 -p $port --dport $i -j SNAT --to aaaa:bbbb:cccc:dddd::1;
ip6tables -A FORWARD -s fd42:42:42::2 -p $port --dport $i -j ACCEPT;
ip6tables -A FORWARD -d fd42:42:42::2 -p $port --dport $i -j ACCEPT;
done
iptables -t nat -A PREROUTING -i eth0 -p $port --dport 49153:49193 -j DNAT --to-destination 10.6.0.2;
iptables -t nat -A POSTROUTING -s 10.6.0.2 -p $port --dport 49153:49193 -j SNAT --to 98.76.543.210;
iptables -A FORWARD -s 10.6.0.2 -p $port --dport 49153:49193 -j ACCEPT;
iptables -A FORWARD -d 10.6.0.2 -p $port --dport 49153:49193 -j ACCEPT;
ip6tables -t nat -A PREROUTING -i eth0 -p $port --dport 49153:49193 -j DNAT --to-destination fd42:42:42::2;
ip6tables -t nat -A POSTROUTING -s fd42:42:42::2 -p $port --dport 49153:49193 -j SNAT --to aaaa:bbbb:cccc:dddd::1;
ip6tables -A FORWARD -s fd42:42:42::2 -p $port --dport 49153:49193 -j ACCEPT;
ip6tables -A FORWARD -d fd42:42:42::2 -p $port --dport 49153:49193 -j ACCEPT;
done
# PostDown.sh VPS
iptables -D FORWARD -i wg0 -j ACCEPT;
iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE;
ip6tables -D FORWARD -i wg0 -j ACCEPT;
ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE;
# icmp
iptables -D INPUT -p icmp -j ACCEPT;
ip6tables -D INPUT -p ipv6-icmp -j ACCEPT;
# Routing TCP port 25 and 587 from Yunohost Server to internet
for j in 25 587 5350 5349 49153:49193
do
iptables -t nat -D POSTROUTING -s 10.6.0.2 -p tcp --dport $j -j SNAT --to 98.76.543.210;
iptables -D FORWARD -s 10.6.0.2 -p tcp --dport $j -j ACCEPT;
ip6tables -t nat -D POSTROUTING -s fd42:42:42::2 -p tcp --dport $j -j SNAT --to aaaa:bbbb:cccc:dddd::1;
ip6tables -D FORWARD -s fd42:42:42::2 -p tcp --dport $j -j ACCEPT;
done
# Routing TCP port required from VPN server to Yunohost server
for i in 25 80 140 443 587 993 5222 5269 8448
do
iptables -t nat -D PREROUTING -i eth0 -p tcp --dport $i -j DNAT --to-destination 10.6.0.2;
iptables -D FORWARD -d 10.6.0.2 -p tcp --dport $i -j ACCEPT;
ip6tables -t nat -D PREROUTING -i eth0 -p tcp --dport $i -j DNAT --to-destination fd42:42:42::2;
ip6tables -D FORWARD -d fd42:42:42::2 -p tcp --dport $i -j ACCEPT;
done
# synapse contur
for port in udp tcp
do
for i in 5350 5349
do
iptables -D FORWARD -s 10.6.0.2 -p $port --dport $i -j ACCEPT;
iptables -D FORWARD -d 10.6.0.2 -p $port --dport $i -j ACCEPT;
iptables -t nat -D PREROUTING -i eth0 -p $port --dport $i -j DNAT --to-destination 10.6.0.2;
iptables -t nat -D POSTROUTING -s 10.6.0.2 -p $port --dport $i -j SNAT --to 98.76.543.210;
ip6tables -D FORWARD -s fd42:42:42::2 -p $port --dport $i -j ACCEPT;
ip6tables -D FORWARD -d fd42:42:42::2 -p $port --dport $i -j ACCEPT;
ip6tables -t nat -D PREROUTING -i eth0 -p $port --dport $i -j DNAT --to-destination fd42:42:42::2;
ip6tables -t nat -D POSTROUTING -s fd42:42:42::2 -p $port --dport $i -j SNAT --to aaaa:bbbb:cccc:dddd::1;
done
iptables -D FORWARD -s 10.6.0.2 -p $port --dport 49153:49193 -j ACCEPT;
iptables -D FORWARD -d 10.6.0.2 -p $port --dport 49153:49193 -j ACCEPT;
iptables -t nat -D PREROUTING -i eth0 -p $port --dport 49153:49193 -j DNAT --to-destination 10.6.0.2;
iptables -t nat -D POSTROUTING -s 10.6.0.2 -p $port --dport 49153:49193 -j SNAT --to 98.76.543.210;
ip6tables -D FORWARD -s fd42:42:42::2 -p $port --dport 49153:49193 -j ACCEPT;
ip6tables -D FORWARD -d fd42:42:42::2 -p $port --dport 49153:49193 -j ACCEPT;
ip6tables -t nat -D PREROUTING -i eth0 -p $port --dport 49153:49193 -j DNAT --to-destination fd42:42:42::2;
ip6tables -t nat -D POSTROUTING -s fd42:42:42::2 -p $port --dport 49153:49193 -j SNAT --to aaaa:bbbb:cccc:dddd::1;
done
YH settings
# PostUp.sh Yunohost
#Begin IPV4
iptables -w -N vpnclient_in;
iptables -w -N vpnclient_out;
iptables -w -N vpnclient_fwd;
iptables -w -A vpnclient_in -p icmp -j ACCEPT;
iptables -w -A vpnclient_in -s 10.6.0.2/24 -j ACCEPT;
#Allowing required TCP ports
for i in 25 80 140 443 587 993 5222 5269 8448
do
iptables -w -A vpnclient_in -p tcp --dport $i -j ACCEPT;
done
#Allowing required Synapse Contur ports
iptables -w -A vpnclient_in --dport 5349 -j ACCEPT;
iptables -w -A vpnclient_in --dport 5350 -j ACCEPT;
iptables -w -A vpnclient_in --dport 49153:49193 -j ACCEPT;
#end synapse
iptables -w -A vpnclient_in -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT;
iptables -w -A vpnclient_in -j DROP;
iptables -w -A vpnclient_out -j ACCEPT;
iptables -w -A vpnclient_fwd -j DROP;
iptables -w -I INPUT 1 -i wg0 -j vpnclient_in;
iptables -w -I OUTPUT 1 -o wg0 -j vpnclient_out;
iptables -w -I FORWARD 1 -o wg0 -j vpnclient_fwd;
#End IPV4
#Begin IPV6
ip6tables -w -N vpnclient_in;
ip6tables -w -N vpnclient_out;
ip6tables -w -N vpnclient_fwd;
ip6tables -w -A vpnclient_in -p ipv6-icmp -j ACCEPT;
ip6tables -w -A vpnclient_in -s fd42:42:42::2/64 -j ACCEPT;
#Allowing required TCP ports
for i in 25 80 140 443 587 993 5222 5269 8448
do
ip6tables -w -A vpnclient_in -p tcp --dport $i -j ACCEPT;
done
#Allowing required Synapse Contur ports
ip6tables -w -A vpnclient_in --dport 5349 -j ACCEPT;
ip6tables -w -A vpnclient_in --dport 5350 -j ACCEPT;
ip6tables -w -A vpnclient_in --dport 49153:49193 -j ACCEPT;
#end synapse
ip6tables -w -A vpnclient_in -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT;
ip6tables -w -A vpnclient_in -j DROP;
ip6tables -w -A vpnclient_out -j ACCEPT;
ip6tables -w -A vpnclient_fwd -j DROP;
ip6tables -w -I INPUT 1 -i wg0 -j vpnclient_in;
ip6tables -w -I OUTPUT 1 -o wg0 -j vpnclient_out;
ip6tables -w -I FORWARD 1 -o wg0 -j vpnclient_fwd;
#End IPV6
# PostDown.sh YH
#Begin IPV4
iptables -w -F vpnclient_in;
iptables -w -F vpnclient_out;
iptables -w -F vpnclient_fwd;
iptables -D INPUT -i wg0 -j vpnclient_in;
iptables -D FORWARD -o wg0 -j vpnclient_fwd;
iptables -D OUTPUT -o wg0 -j vpnclient_out;
iptables -w -X vpnclient_in;
iptables -w -X vpnclient_out;
iptables -w -X vpnclient_fwd;
#End IPV4
#Begin IPV6
ip6tables -w -F vpnclient_in;
ip6tables -w -F vpnclient_out;
ip6tables -w -F vpnclient_fwd;
ip6tables -D INPUT -i wg0 -j vpnclient_in;
ip6tables -D FORWARD -o wg0 -j vpnclient_fwd;
ip6tables -D OUTPUT -o wg0 -j vpnclient_out;
ip6tables -w -X vpnclient_in;
ip6tables -w -X vpnclient_out;
ip6tables -w -X vpnclient_fwd;
#End IPV6
Some port testing to see that its correct.
Testing VPS
# iptables-save | grep 5349
-A PREROUTING -i eth0 -p udp -m udp --dport 5349 -j DNAT --to-destination 10.6.0.2
-A PREROUTING -i eth0 -p tcp -m tcp --dport 5349 -j DNAT --to-destination 10.6.0.2
-A POSTROUTING -s 10.6.0.2/32 -p udp -m udp --dport 5349 -j SNAT --to-source 98.76.543.210
-A POSTROUTING -s 10.6.0.2/32 -p tcp -m tcp --dport 5349 -j SNAT --to-source 98.76.543.210
-A FORWARD -s 10.6.0.2/32 -p udp -m udp --dport 5349 -j ACCEPT
-A FORWARD -d 10.6.0.2/32 -p udp -m udp --dport 5349 -j ACCEPT
-A FORWARD -s 10.6.0.2/32 -p tcp -m tcp --dport 5349 -j ACCEPT
-A FORWARD -d 10.6.0.2/32 -p tcp -m tcp --dport 5349 -j ACCEPT
Testing YH
# iptables-save | grep 5349
-A INPUT -p tcp -m tcp --dport 5349 -j ACCEPT
-A INPUT -p udp -m udp --dport 5349 -j ACCEPT
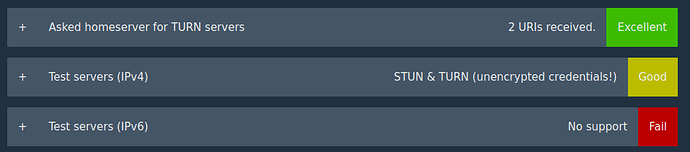
Matrix VoIP Tester
(Im not sure why ip6 fails…?)
edit: fixed two faulty port numbers in the PostUp.sh Yunohost, changed from 5439 to 5349