My YunoHost server
Hardware: Old laptop or computer
YunoHost version: 11.2.8.2 (stable)
I have access to my server : SSH | webadmin | direct access |
Are you in a special context? : I don’t think so.
Problem Apps:
- Bludit 3.15.0~ynh2
- SearxNG 2023.11.29.00.14.42~ynh1
Description of the Issue
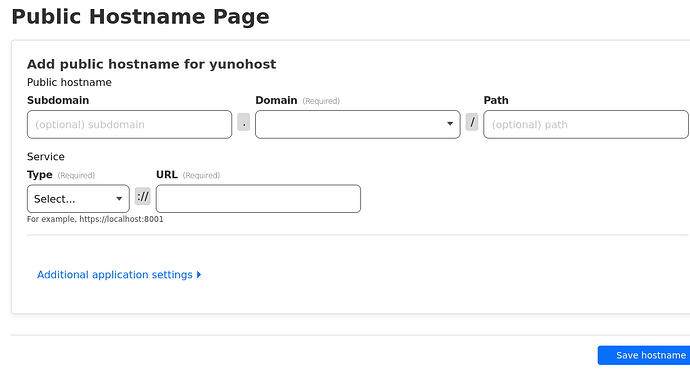
I am trying to set up my Yunohost instance through Cloudflare Zero Trust. To do this, I need to know the local address that the aforementioned apps are listening on (Something like localhost:8001).
To find this out, I have checked my nginx configs, and nearly all the files in the locations at /var/www/searxng/searxng-src/.
I have also used netstat -tunlp to check every one of the ports that my machine is listening on with curl http://localhost:<portnumber>.
The Dockerfile of SearxNG seems to indicate that it is listening on Port 8080.
I have tried setting this along with every port listed in the output from netstat in curl and nothing is responding as expected.
Context
Here is the output from netstat
Steps to reproduce
On a machine running this package, run curl localhost:<portnumber> on any of the port numbers listed by netstat.
Expected behavior
curl is expected to return the HTML of the front page for SearxNG when using localhost or 127.0.0.1. With one of the listening ports.
It is returning anything but that.
curl is expected to return the HTML of the front page for Bludit when using localhost or 127.0.0.1. With one of the listening ports.
It is returning anything but that.
TIA
I have been working on this for several days, trying to learn as much as I can. I have read many blogs, including the confusing articles in Cloudflare’s docs. I realize this is a skill issue. There is probably something very basic that I am missing.
Furthermore, I am not a great troubleshooter. Any help is greatly appreciated. Anything you can offer will help me take advantage of self-hosting, this awesome service.
Thank you to all who help maintain this great resource that allows us to take back our data. ![]()
FWIW
I was able to find the ports of:
- Pleroma
- Gitea
- Standard Notes
- Filebrowser
Using the netstat + curl method described earlier. I have successfully set them up, and they are accessible through CF’s Zero Trust.