What type of hardware are you using: Virtual machine
What YunoHost version are you running: 12.1.28
How are you able to access your server: The webadmin
Describe your issue
Bonjour,
Comme le collègue de ce sujet Utbound mail to blocked: Spamhaus “open resolver” return code – need help with YunoHost DNS/Rspamd setup - #8 by AT69 J’ai aussi un problème avec ce " Error: open resolver".
j’ai reçu hier matin le mail de diagnostique yunohost me signalant une erreur:
=================================
Email (mail)
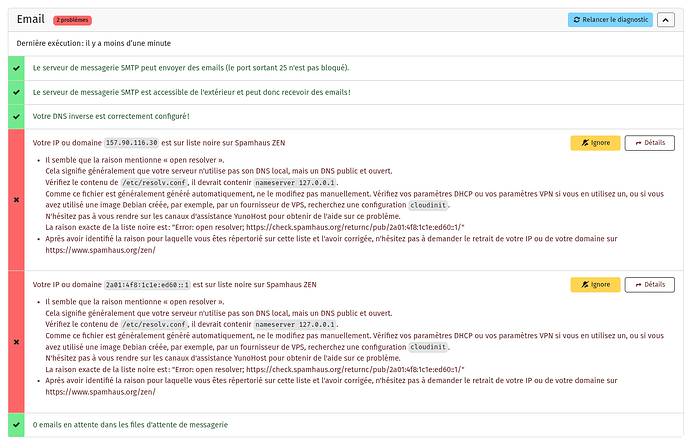
[ERROR] Your IP or domain XX.XX.XX.XX is blacklisted on Spamhaus ZEN
- The blacklist reason is: “Error: open resolver; https://check.spamhaus.org/returnc/pub/2001:19f0:5000:1800:5400:5ff:fe01:2dc5/”
- After identifying why you are listed and fixing it, feel free to ask for your IP or domain to be removed on ZEN Blocklist | Combined IP DNSBLs for effective email filtering
Le même mail reçu hier soir mais étrangement, rien ce matin (pourtant encore présent dans le diagnostique).
Contrairement au sujet cité, je n’ai pas activé l’antispam de yunohost, par contre, je n’ai pas de problème pour envoyer ou recevoir des mails (testé depuis et vers mes comptes Hotmail et pro (microsoft)).
J’ai aussi vérifié et je suis blacklisté sur https://rbldns.ru Le port 53 de yunohost était ouvert (je l’ai fermé à l’instant) mais ce port n’est pas routé vers l’extérieur (yuno est derrière un routeur Opnsense en DMZ sur la Freebox )
Un ami a exactement le même problème.
Une idée de pourquoi j’ai ce message ?
Share relevant logs or error messages
The automatic diagnosis on your YunoHost server identified some issues on your server. You will find a description of the issues below. You can manage those issues in the ‘Diagnosis’ section in your webadmin.
=================================
Email (mail)
[ERROR] Your IP or domain XX.XX.XX.XX is blacklisted on Spamhaus ZEN
- The blacklist reason is: “Error: open resolver; https://check.spamhaus.org/returnc/pub/2001:19f0:5000:1800:5400:5ff:fe01:2dc5/”
- After identifying why you are listed and fixing it, feel free to ask for your IP or domain to be removed on ZEN Blocklist | Combined IP DNSBLs for effective email filtering