mx4k
March 7, 2023, 11:23am
1
Good time of the day. I’ve already set up Yunohost in a VM.
The Server isn’t reachable from the internet and never will be.
Unfortunately every browser on my windows machine doesn’t like the selft signed certificate.
How can I prevent the browser from warning about the certificate?
You need to download the Certification Authority certificate of your server and install it into your Windows machine.
It is located at /etc/ssl/certs/ca-yunohost_crt.pem.
2 Likes
mx4k
March 7, 2023, 1:29pm
3
I have copied the file to /tmp and downloaded it with scp.
certutil -addstore -v -f "Root" .\ca-yunohost_crt.pem
The result of
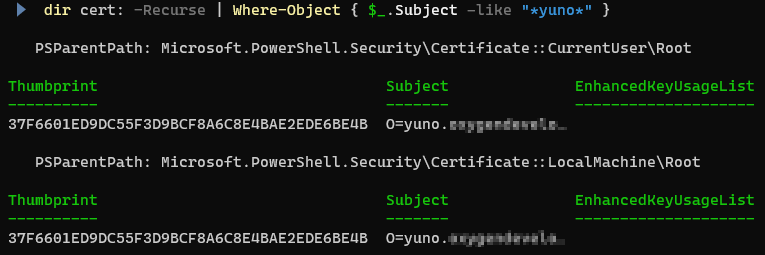
dir cert: -Recurse | Where-Object { $_.Subject -like "*yuno*" }
is this
But still no browser accepts the certificate… I don’t get it.
Can you check that the certificate issuer from your browser warning screen is indeed the same as the one you downloaded?
mx4k
March 7, 2023, 8:38pm
6
Thank you very much for your effort so far! I really appreciate this!
It’s strange but they seem different:
maxim@yuno:~$ sudo openssl x509 -noout -fingerprint -sha1 -inform pem -in /etc/ssl/certs/ca-yunohost_crt.pem
SHA1 Fingerprint=37:F6:60:1E:D9:DC:55:F3:D9:BC:F8:A6:C8:E4:BA:E2:ED:E6:BE:4B
maxim@yuno:~$ openssl s_client -connect yuno.mydomain.com:443 < /dev/null 2>/dev/null | openssl x509 -text -fingerprint -sha1 -inform pem -in /dev/stdin | grep SHA1
SHA1 Fingerprint=8B:A2:88:1D:6A:6F:2A:61:4A:D2:48:04:5A:0F:25:83:C7:38:1A:4F
Weird indeed! Can you try with /etc/ssl/certs/ca-yunohost_crt.pem instead?
mx4k
March 9, 2023, 10:34am
8
I’m sorry, I don’t really understand what to try with this certificate file. Can you please explain a little further?
mx4k
March 9, 2023, 1:21pm
9
So, I’ve figured it out, how to get this working.
Powershell:
$own_domain = yuno.owndomain.com
$own_ca_name = "My Root CA"
$rootCA = New-SelfSignedCertificate -Subject "CN=$own_ca_name" `
-KeyExportPolicy Exportable `
-KeyUsage CertSign,CRLSign,DigitalSignature `
-KeyLength 2048 `
-KeyUsageProperty All `
-KeyAlgorithm 'RSA' `
-HashAlgorithm 'SHA256' `
-Provider "Microsoft Enhanced RSA and AES Cryptographic Provider" `
-NotAfter (Get-Date).AddYears(10)
New-SelfSignedCertificate -Subject "CN=$own_domain" `
-Signer $rootCA `
-KeyLength 2048 `
-KeyExportPolicy Exportable `
-DnsName $own_domain `
-KeyAlgorithm 'RSA' `
-HashAlgorithm 'SHA256' `
-Provider "Microsoft Enhanced RSA and AES Cryptographic Provider" `
-NotAfter (Get-Date).AddYears(2)
Export the certificate with private certificate and password. Move the root ca to trusted root certificate.
SSH:
# Own Domain please update
own_domain = yuno.owndomain.com
# Extract encrypted RSA Key from .pfx file
openssl pkcs12 -in yuno.owndomain.com.pfx -nocerts -out ssl_crypt.key
# Remove Encryption from RSA Key
openssl rsa -in ssl_crypt.key -out ssl.key
# Delete encrypted RSA Key
rm ssl_crypt.key
# Extract Public Certificate from .pfx file
openssl pkcs12 -in yuno.owndomain.com.pfx -clcerts -nokeys -out ssl.crt
# Extract CA Chain from .pfx file
openssl pkcs12 -in yuno.owndomain.com.pfx -cacerts -nokeys -chain -out ca.pem
# Create folder for new certificate files and move these
sudo mkdir /etc/yunohost/certs/$own_domain/ae_certs
sudo mv ssl.key ssl.crt ca.pem /etc/yunohost/$own_domain/DOMAIN.TLD/ae_certs/
# Gain root
sudo -i
# Move to cert location
cd /etc/yunohost/certs/$own_domain/
# Move old certificate files
mkdir yunohost_self_signed
mv *.pem *.cnf yunohost_self_signed/
# Combine root certificate with public certificate to create a unified certificate chain
cat ae_certs/ssl.crt ae_certs/ca.pem | sudo tee crt.pem
# Convert private key to .pem format
sudo openssl rsa -in ae_certs/ssl.key -out key.pem -outform PEM
# secure your certificate files
sudo chown root:metronome crt.pem key.pem
sudo chmod 640 crt.pem key.pem
sudo chown root:root -R ae_certs
sudo chmod 600 -R ae_certs
# Copy the new certificates
cp ae_certs/*.pem ./
# Restart NGINX
sudo service nginx reload
Hello mx4k,
I am removing the Solved tag for now.
Your solution is way overkill: you create a new certification authority and have it sign new certificates, while I am merely trying to have you download and install the existing certification authority created by YunoHost.
And your solution will not extend to new subdomains, unless you redo this whole process again.
By this I meant “follow the instructions of my first message with that file instead.”
system
March 25, 2023, 4:55am
12
This topic was automatically closed 15 days after the last reply. New replies are no longer allowed.