English version below
Bonjour, depuis peu, j’ai un souci d’accès SSH et SFTP à mon serveur Yunohost.
Description du problème
Je viens d’installer sur un serveur dédié tout neuf mon instance Yunohost. Tout se passait bien, j’accède au serveur en SSH sans désagréments.
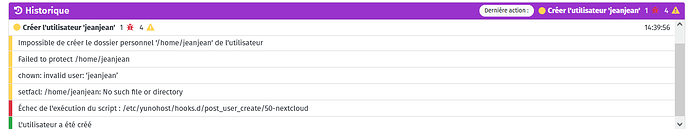
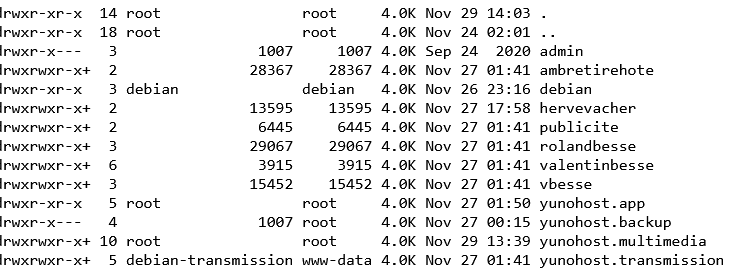
Ce midi, je reboot mon serveur juste après avoir rajouté un compte utilisateur (syncthing) à un groupe pour que le soft ait accès à un répertoire en lecture.
Depuis impossible de me connecter en ssh.
Voici le contenu du log ssh :
LOGFILE: journalctl
-- Journal begins at Sat 2022-11-26 22:58:44 UTC, ends at Tue 2022-11-29 13:08:20 UTC. --
Nov 29 12:29:39 sshd[1690]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:29:39 sshd[1690]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:29:41 sshd[1690]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46663 ssh2
Nov 29 12:29:44 sshd[1690]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:29:44 sshd[1690]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:29:46 sshd[1690]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46663 ssh2
Nov 29 12:30:09 sshd[1790]: Connection from 37.166.209.129 port 46633 on 192.99.13.119 port 1988 rdomain ""
Nov 29 12:30:10 sshd[1790]: Invalid user valentinbesse from 37.166.209.129 port 46633
Nov 29 12:30:10 sshd[1790]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:30:10 sshd[1790]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:30:10 sshd[1790]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:30:12 sshd[1790]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46633 ssh2
Nov 29 12:30:14 sshd[1790]: Connection reset by invalid user valentinbesse 37.166.209.129 port 46633 [preauth]
Nov 29 12:54:08 sshd[785]: Received signal 15; terminating.
Nov 29 12:54:08 systemd[1]: Stopping OpenBSD Secure Shell server...
Nov 29 12:54:08 systemd[1]: ssh.service: Succeeded.
Nov 29 12:54:08 systemd[1]: Stopped OpenBSD Secure Shell server.
Nov 29 12:54:08 systemd[1]: Starting OpenBSD Secure Shell server...
Nov 29 12:54:09 sshd[4848]: Server listening on 0.0.0.0 port 1988.
Nov 29 12:54:09 sshd[4848]: Server listening on :: port 1988.
Nov 29 12:54:09 systemd[1]: Started OpenBSD Secure Shell server.
Nov 29 12:55:37 systemd[1]: Stopping OpenBSD Secure Shell server...
Nov 29 12:55:37 systemd[1]: ssh.service: Succeeded.
Nov 29 12:55:37 systemd[1]: Stopped OpenBSD Secure Shell server.
-- Boot 3c8447e2b7364354840748ff6529ef21 --
Nov 29 12:56:51 systemd[1]: Starting OpenBSD Secure Shell server...
Nov 29 12:56:51 sshd[680]: Server listening on 0.0.0.0 port 1988.
Nov 29 12:56:51 sshd[680]: Server listening on :: port 1988.
Nov 29 12:56:51 systemd[1]: Started OpenBSD Secure Shell server.
Nov 29 12:57:24 sshd[1594]: Connection from 37.166.209.129 port 46684 on 192.99.13.119 port 1988 rdomain ""
Nov 29 12:57:24 sshd[1594]: Invalid user valentinbesse from 37.166.209.129 port 46684
Nov 29 12:57:25 sshd[1594]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:57:25 sshd[1594]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:57:25 sshd[1594]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:57:26 sshd[1594]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46684 ssh2
Nov 29 12:57:26 sshd[1594]: Connection reset by invalid user valentinbesse 37.166.209.129 port 46684 [preauth]
Nov 29 12:59:36 sshd[680]: Received signal 15; terminating.
Nov 29 12:59:36 systemd[1]: Stopping OpenBSD Secure Shell server...
Nov 29 12:59:36 systemd[1]: ssh.service: Succeeded.
Nov 29 12:59:36 systemd[1]: Stopped OpenBSD Secure Shell server.
Nov 29 12:59:36 systemd[1]: Starting OpenBSD Secure Shell server...
Nov 29 12:59:36 sshd[1704]: Server listening on 0.0.0.0 port 1988.
Nov 29 12:59:36 sshd[1704]: Server listening on :: port 1988.
Nov 29 12:59:36 systemd[1]: Started OpenBSD Secure Shell server.
Nov 29 12:59:42 sshd[1749]: Connection from 37.166.209.129 port 46688 on 192.99.13.119 port 1988 rdomain ""
Nov 29 12:59:43 sshd[1749]: Invalid user valentinbesse from 37.166.209.129 port 46688
Nov 29 12:59:43 sshd[1749]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:59:43 sshd[1749]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:59:43 sshd[1749]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:59:44 sshd[1749]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46688 ssh2
Nov 29 12:59:45 sshd[1749]: Connection reset by invalid user valentinbesse 37.166.209.129 port 46688 [preauth]
Les lignes suivantes sont curieuses :
Nov 29 12:59:43 sshd[1749]: Invalid user valentinbesse from 37.166.209.129 port 46688
Nov 29 12:59:43 sshd[1749]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:59:43 sshd[1749]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:59:43 sshd[1749]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:59:44 sshd[1749]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46688 ssh2
Nov 29 12:59:45 sshd[1749]: Connection reset by invalid user valentinbesse 37.166.209.129 port 46688 [preauth]
Mon fichier sshd_config :
# This configuration has been automatically generated
# by YunoHost
Protocol 2
# PLEASE: if you wish to change the ssh port properly in YunoHost, use this command:
# yunohost settings set security.ssh.port -v <port>
Port 1988
ListenAddress ::
ListenAddress 0.0.0.0
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key
HostKey /etc/ssh/ssh_host_rsa_key
# ##############################################
# Stuff recommended by Mozilla "modern" compat'
# https://infosec.mozilla.org/guidelines/openssh
# ##############################################
# By default use "modern" Mozilla configuration
# Keys, ciphers and MACS
KexAlgorithms curve25519-sha256@libssh.org,ecdh-sha2-nistp521,ecdh-sha2-nistp384,ecdh-sha2-nistp256,diffie-hellman-group-exchange-sha256
Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr
MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-512,hmac-sha2-256,umac-128@openssh.com
# LogLevel VERBOSE logs user's key fingerprint on login.
# Needed to have a clear audit track of which key was using to log in.
SyslogFacility AUTH
LogLevel VERBOSE
# #######################
# Authentication settings
# #######################
# Comment from Mozilla about the motivation behind disabling root login
#
# Root login is not allowed for auditing reasons. This is because it's difficult to track which process belongs to which root user:
#
# On Linux, user sessions are tracking using a kernel-side session id, however, this session id is not recorded by OpenSSH.
# Additionally, only tools such as systemd and auditd record the process session id.
# On other OSes, the user session id is not necessarily recorded at all kernel-side.
# Using regular users in combination with /bin/su or /usr/bin/sudo ensure a clear audit track.
LoginGraceTime 120
PermitRootLogin no
StrictModes yes
PubkeyAuthentication yes
PermitEmptyPasswords no
ChallengeResponseAuthentication no
UsePAM yes
# PLEASE: if you wish to force everybody to authenticate using ssh keys, run this command:
# yunohost settings set security.ssh.password_authentication -v no
#PasswordAuthentication yes
# Post-login stuff
Banner /etc/issue.net
PrintMotd no
PrintLastLog yes
ClientAliveInterval 60
AcceptEnv LANG LC_*
# Disallow user without ssh or sftp permissions
AllowGroups ssh.main sftp.main ssh.app sftp.app admins root
# Allow users to create tunnels or forwarding
AllowTcpForwarding yes
AllowStreamLocalForwarding yes
PermitTunnel yes
PermitUserRC yes
# SFTP stuff
Subsystem sftp internal-sftp
# Apply following instructions to user with sftp perm only
Match Group sftp.main,!ssh.main
ForceCommand internal-sftp
# We can't restrict to /home/%u because the chroot base must be owned by root
# So we chroot only on /home
# See https://serverfault.com/questions/584986/bad-ownership-or-modes-for-chroot-directory-component
ChrootDirectory /home
# Forbid SFTP users from using their account SSH as a VPN (even if SSH login is disabled)
AllowTcpForwarding no
AllowStreamLocalForwarding no
PermitTunnel no
# Disable .ssh/rc, which could be edited (e.g. from Nextcloud or whatever) by users to execute arbitrary commands even if SSH login is disabled
PermitUserRC no
Match Group sftp.app,!ssh.app
ForceCommand internal-sftp
ChrootDirectory %h
AllowTcpForwarding no
AllowStreamLocalForwarding no
PermitTunnel no
PermitUserRC no
PasswordAuthentication yes
# root login is allowed on local networks
# It's meant to be a backup solution in case LDAP is down and
# user admin can't be used...
# If the server is a VPS, it's expected that the owner of the
# server has access to a web console through which to log in.
Match Address 192.168.0.0/16,10.0.0.0/8,172.16.0.0/12,169.254.0.0/16,fe80::/10,fd00::/8
PermitRootLogin yes#
et enfin le fichier nslcd.conf :
# /etc/nslcd.conf
# nslcd configuration file. See nslcd.conf(5)
# for details.
# The user and group nslcd should run as.
uid nslcd
gid nslcd
# The location at which the LDAP server(s) should be reachable.
uri ldap://localhost/
# The search base that will be used for all queries.
base dc=yunohost,dc=org
# The LDAP protocol version to use.
#ldap_version 3
# The DN to bind with for normal lookups.
#binddn cn=annonymous,dc=example,dc=net
#bindpw secret
# The DN used for password modifications by root.
#rootpwmoddn cn=admin,dc=example,dc=com
# SSL options
#ssl off
#tls_reqcert never
tls_cacertfile /etc/ssl/certs/ca-certificates.crt
# The search scope.
#scope sub
# Build a full list of non-LDAP users on startup.
nss_initgroups_ignoreusers ALLLOCAL
# The minimum numeric user id to lookup.
nss_min_uid 1000
# Default Shell for user
man passwd loginShell "/usr/bin/zsh"
Une idée du pourquoi du comment ?
English version
Hello, recently, I have a problem with SSH and SFTP access to my Yunohost server.
Description of the issue
I have just installed on a brand new dedicated server my Yunohost instance. Everything was going well, I can access the server with SSH without any problem.
This afternoon, I rebooted my server just after adding a user account (syncthing) to a group so that the software could have access to a read directory.
Since then I can’t connect with ssh.
Here is the content of the ssh log :
LOGFILE: journalctl
-- Journal begins at Sat 2022-11-26 22:58:44 UTC, ends at Tue 2022-11-29 13:08:20 UTC. --
Nov 29 12:29:39 sshd[1690]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:29:39 sshd[1690]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:29:41 sshd[1690]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46663 ssh2
Nov 29 12:29:44 sshd[1690]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:29:44 sshd[1690]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:29:46 sshd[1690]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46663 ssh2
Nov 29 12:30:09 sshd[1790]: Connection from 37.166.209.129 port 46633 on 192.99.13.119 port 1988 rdomain ""
Nov 29 12:30:10 sshd[1790]: Invalid user valentinbesse from 37.166.209.129 port 46633
Nov 29 12:30:10 sshd[1790]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:30:10 sshd[1790]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:30:10 sshd[1790]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:30:12 sshd[1790]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46633 ssh2
Nov 29 12:30:14 sshd[1790]: Connection reset by invalid user valentinbesse 37.166.209.129 port 46633 [preauth]
Nov 29 12:54:08 sshd[785]: Received signal 15; terminating.
Nov 29 12:54:08 systemd[1]: Stopping OpenBSD Secure Shell server...
Nov 29 12:54:08 systemd[1]: ssh.service: Succeeded.
Nov 29 12:54:08 systemd[1]: Stopped OpenBSD Secure Shell server.
Nov 29 12:54:08 systemd[1]: Starting OpenBSD Secure Shell server...
Nov 29 12:54:09 sshd[4848]: Server listening on 0.0.0.0 port 1988.
Nov 29 12:54:09 sshd[4848]: Server listening on :: port 1988.
Nov 29 12:54:09 systemd[1]: Started OpenBSD Secure Shell server.
Nov 29 12:55:37 systemd[1]: Stopping OpenBSD Secure Shell server...
Nov 29 12:55:37 systemd[1]: ssh.service: Succeeded.
Nov 29 12:55:37 systemd[1]: Stopped OpenBSD Secure Shell server.
-- Boot 3c8447e2b7364354840748ff6529ef21 --
Nov 29 12:56:51 systemd[1]: Starting OpenBSD Secure Shell server...
Nov 29 12:56:51 sshd[680]: Server listening on 0.0.0.0 port 1988.
Nov 29 12:56:51 sshd[680]: Server listening on :: port 1988.
Nov 29 12:56:51 systemd[1]: Started OpenBSD Secure Shell server.
Nov 29 12:57:24 sshd[1594]: Connection from 37.166.209.129 port 46684 on 192.99.13.119 port 1988 rdomain ""
Nov 29 12:57:24 sshd[1594]: Invalid user valentinbesse from 37.166.209.129 port 46684
Nov 29 12:57:25 sshd[1594]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:57:25 sshd[1594]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:57:25 sshd[1594]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:57:26 sshd[1594]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46684 ssh2
Nov 29 12:57:26 sshd[1594]: Connection reset by invalid user valentinbesse 37.166.209.129 port 46684 [preauth]
Nov 29 12:59:36 sshd[680]: Received signal 15; terminating.
Nov 29 12:59:36 systemd[1]: Stopping OpenBSD Secure Shell server...
Nov 29 12:59:36 systemd[1]: ssh.service: Succeeded.
Nov 29 12:59:36 systemd[1]: Stopped OpenBSD Secure Shell server.
Nov 29 12:59:36 systemd[1]: Starting OpenBSD Secure Shell server...
Nov 29 12:59:36 sshd[1704]: Server listening on 0.0.0.0 port 1988.
Nov 29 12:59:36 sshd[1704]: Server listening on :: port 1988.
Nov 29 12:59:36 systemd[1]: Started OpenBSD Secure Shell server.
Nov 29 12:59:42 sshd[1749]: Connection from 37.166.209.129 port 46688 on 192.99.13.119 port 1988 rdomain ""
Nov 29 12:59:43 sshd[1749]: Invalid user valentinbesse from 37.166.209.129 port 46688
Nov 29 12:59:43 sshd[1749]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:59:43 sshd[1749]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:59:43 sshd[1749]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:59:44 sshd[1749]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46688 ssh2
Nov 29 12:59:45 sshd[1749]: Connection reset by invalid user valentinbesse 37.166.209.129 port 46688 [preauth]
These lines are weird:
Nov 29 12:59:43 sshd[1749]: Invalid user valentinbesse from 37.166.209.129 port 46688
Nov 29 12:59:43 sshd[1749]: pam_unix(sshd:auth): check pass; user unknown
Nov 29 12:59:43 sshd[1749]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=37.166.209.129
Nov 29 12:59:43 sshd[1749]: pam_ldap(sshd:auth): error opening connection to nslcd: No such file or directory
Nov 29 12:59:44 sshd[1749]: Failed password for invalid user valentinbesse from 37.166.209.129 port 46688 ssh2
Nov 29 12:59:45 sshd[1749]: Connection reset by invalid user valentinbesse 37.166.209.129 port 46688 [preauth]
Heren, my sshd_config:
# This configuration has been automatically generated
# by YunoHost
Protocol 2
# PLEASE: if you wish to change the ssh port properly in YunoHost, use this command:
# yunohost settings set security.ssh.port -v <port>
Port 1988
ListenAddress ::
ListenAddress 0.0.0.0
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key
HostKey /etc/ssh/ssh_host_rsa_key
# ##############################################
# Stuff recommended by Mozilla "modern" compat'
# https://infosec.mozilla.org/guidelines/openssh
# ##############################################
# By default use "modern" Mozilla configuration
# Keys, ciphers and MACS
KexAlgorithms curve25519-sha256@libssh.org,ecdh-sha2-nistp521,ecdh-sha2-nistp384,ecdh-sha2-nistp256,diffie-hellman-group-exchange-sha256
Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr
MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-512,hmac-sha2-256,umac-128@openssh.com
# LogLevel VERBOSE logs user's key fingerprint on login.
# Needed to have a clear audit track of which key was using to log in.
SyslogFacility AUTH
LogLevel VERBOSE
# #######################
# Authentication settings
# #######################
# Comment from Mozilla about the motivation behind disabling root login
#
# Root login is not allowed for auditing reasons. This is because it's difficult to track which process belongs to which root user:
#
# On Linux, user sessions are tracking using a kernel-side session id, however, this session id is not recorded by OpenSSH.
# Additionally, only tools such as systemd and auditd record the process session id.
# On other OSes, the user session id is not necessarily recorded at all kernel-side.
# Using regular users in combination with /bin/su or /usr/bin/sudo ensure a clear audit track.
LoginGraceTime 120
PermitRootLogin no
StrictModes yes
PubkeyAuthentication yes
PermitEmptyPasswords no
ChallengeResponseAuthentication no
UsePAM yes
# PLEASE: if you wish to force everybody to authenticate using ssh keys, run this command:
# yunohost settings set security.ssh.password_authentication -v no
#PasswordAuthentication yes
# Post-login stuff
Banner /etc/issue.net
PrintMotd no
PrintLastLog yes
ClientAliveInterval 60
AcceptEnv LANG LC_*
# Disallow user without ssh or sftp permissions
AllowGroups ssh.main sftp.main ssh.app sftp.app admins root
# Allow users to create tunnels or forwarding
AllowTcpForwarding yes
AllowStreamLocalForwarding yes
PermitTunnel yes
PermitUserRC yes
# SFTP stuff
Subsystem sftp internal-sftp
# Apply following instructions to user with sftp perm only
Match Group sftp.main,!ssh.main
ForceCommand internal-sftp
# We can't restrict to /home/%u because the chroot base must be owned by root
# So we chroot only on /home
# See https://serverfault.com/questions/584986/bad-ownership-or-modes-for-chroot-directory-component
ChrootDirectory /home
# Forbid SFTP users from using their account SSH as a VPN (even if SSH login is disabled)
AllowTcpForwarding no
AllowStreamLocalForwarding no
PermitTunnel no
# Disable .ssh/rc, which could be edited (e.g. from Nextcloud or whatever) by users to execute arbitrary commands even if SSH login is disabled
PermitUserRC no
Match Group sftp.app,!ssh.app
ForceCommand internal-sftp
ChrootDirectory %h
AllowTcpForwarding no
AllowStreamLocalForwarding no
PermitTunnel no
PermitUserRC no
PasswordAuthentication yes
# root login is allowed on local networks
# It's meant to be a backup solution in case LDAP is down and
# user admin can't be used...
# If the server is a VPS, it's expected that the owner of the
# server has access to a web console through which to log in.
Match Address 192.168.0.0/16,10.0.0.0/8,172.16.0.0/12,169.254.0.0/16,fe80::/10,fd00::/8
PermitRootLogin yes#
And finaly, my file nslcd.conf :
# /etc/nslcd.conf
# nslcd configuration file. See nslcd.conf(5)
# for details.
# The user and group nslcd should run as.
uid nslcd
gid nslcd
# The location at which the LDAP server(s) should be reachable.
uri ldap://localhost/
# The search base that will be used for all queries.
base dc=yunohost,dc=org
# The LDAP protocol version to use.
#ldap_version 3
# The DN to bind with for normal lookups.
#binddn cn=annonymous,dc=example,dc=net
#bindpw secret
# The DN used for password modifications by root.
#rootpwmoddn cn=admin,dc=example,dc=com
# SSL options
#ssl off
#tls_reqcert never
tls_cacertfile /etc/ssl/certs/ca-certificates.crt
# The search scope.
#scope sub
# Build a full list of non-LDAP users on startup.
nss_initgroups_ignoreusers ALLLOCAL
# The minimum numeric user id to lookup.
nss_min_uid 1000
# Default Shell for user
man passwd loginShell "/usr/bin/zsh"
Do you know what is going on ? And how to solve it ?
Mon serveur YunoHost / My Yunohost Server
Matériel : Serveur dédié OVH - bare-metal amd64
Version de YunoHost: 11.0.10.2
J’ai accès à mon serveur / access to the serveur : via Root sur Shell In A Box ou WebAdmin
Êtes-vous dans un contexte particulier ou avez-vous effectué des modificiations particulières sur votre instance ? / Any modification : J’ai exécuté les commandes :
sudo yunohost settings set security.nginx.compatibility -v modern
et
sudo yunohost settings set security.ssh.compatibility -v modern
J’ai aussi modifié le fichier